SharePoint Online Connector Configuration (6.1)
This article describes the steps needed for configuring the SharePoint Online Connector (SPOC) after the installation has succeeded.
1. Configure Primary Account for SPOC (Web Interface Access)
The Administrator account must first be created before the SharePoint Online Connector can be configured.
Navigate to https://[your-server]:[port number]
Verify the interface loads correctly
Set up the Administrator user for SPOC
The Administrator password is set on the first login
Click on the Login drop-down button
Choose Login Locally
Enter Administrator for the Email field
Enter a password of your choosing. (Note: The password must be at least 12 characters)
Click Login
The Administrator account can be used to provision new Users as well as manage any aspect of the connector. This account information should be kept secure.
2. Configure Connection to Gimmal Records
This section configures the communication between the SharePoint Online Connector and Gimmal Records.
Access Web Interface: Navigate to https://your-server:8083 (Note: the port will depend on what was chosen during installation)
Connection Management: Go to Connection Configuration > Gimmal Records
Enter Configuration:
URL: URL for the Gimmal Records application
Username: Gimmal Records connector service account username
Password: Gimmal Records connector service account password
3. Configure Microsoft Graph API Connection in the SharePoint Online Connector
This section configures the connection to the Microsoft Graph API used to authenticate to SharePoint.
Click on ‘Microsoft Graph API’ in the left panel
Enter the Tenant ID and Client ID from the App Registration step:
Tenant ID: Your Azure AD Directory (tenant) ID (A)
Client ID: Your Azure AD Application (client) ID (B)
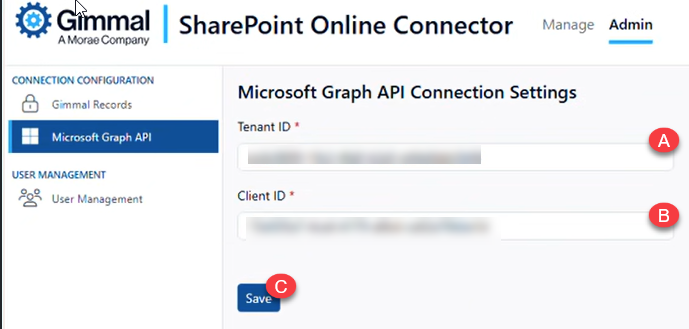
Click the ‘Save’ button (C)
An Upload Certificate button will appear. Click it to upload the .PFX version of the certificate file used during App Registration.
Upload the .PFX certificate file created during App Registration using the ‘Select File’ button (A)
Enter the certificate password (B)
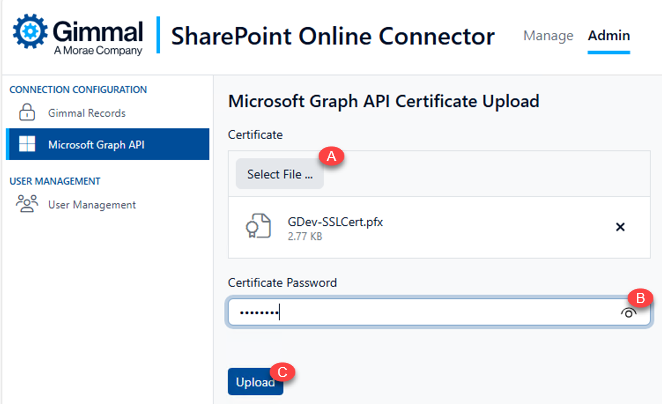
Click the ‘Upload’ button to complete the certificate upload (C)
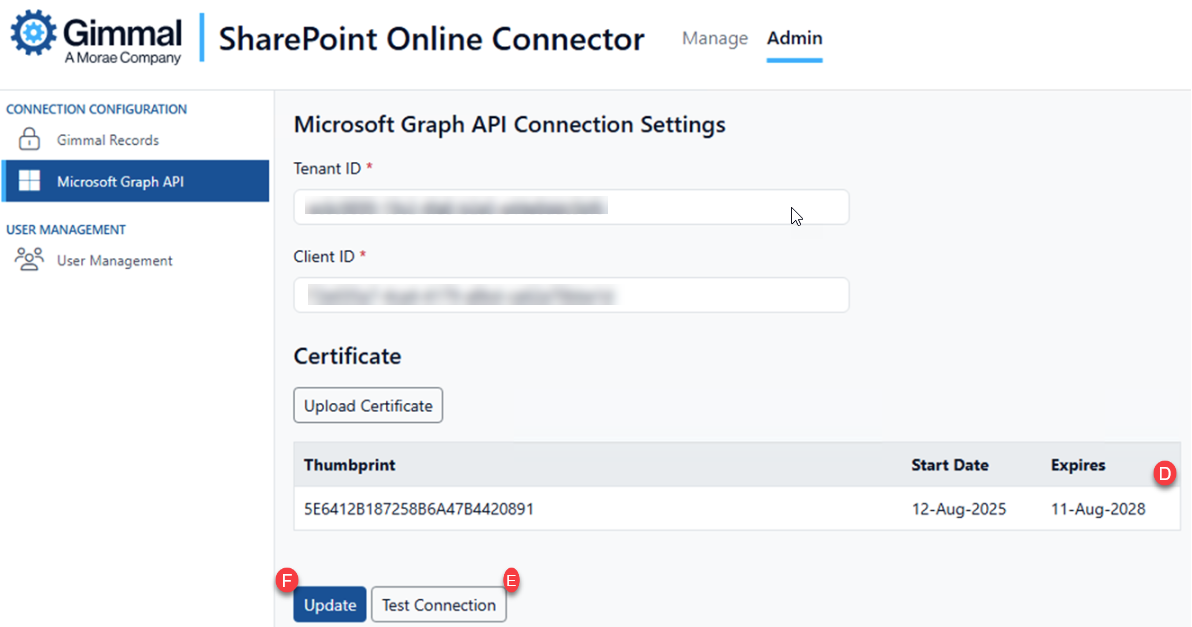
Verify the certificate thumbprint and expiration dates match the original (D)
Test Connection: Click “Test Connection” to validate authentication (E)
Save Configuration: Click ‘Update’ to save the settings (F)
Troubleshooting
Common Installation Issues
SSL Certificate Errors:
Ensure the certificate is properly bound to the IIS site
Verify that the certificate is not expired and includes the server name
Check certificate chain and root CA trust
Service Account Permissions
Verify the service account has the ‘Log on as a Service’ right
Ensure the service account has database permissions
Check the IIS application pool identity permissions
Database Connection Issues
Test SQL Server connectivity from the server
Verify connection string format and credentials
Check SQL Server authentication mode (Windows/Mixed)
Ensure the database exists and is properly configured
Ensure the service account has database permissions
Azure AD Authentication Failures
Verify Tenant ID and Client ID are correct
Check that the certificate is properly uploaded and not expired
Ensure Azure AD app has required Microsoft Graph permissions
Log File Locations
Application Logs: C:\Program Files\Gimmal Records\Logs
Service Logs: Windows Event Log > Application
IIS Logs: C:\inetpub\logs\LogFiles
Installation Logs: MSI log files created during installation
