Platform Overview
Introduction
Gimmal Discover empowers organizations to fully leverage their most critical asset: information. This innovative product offers a comprehensive suite of tools—including Data Governance, eDiscovery, and Classification—that streamline the management of both unstructured and structured data across various repositories. This document outlines the architecture of Gimmal Discover and provides a detailed examination of the capabilities of each component, allowing readers to thoroughly grasp how Discover enhances information management.
Discover Use Cases
This document provides an overview of the Discover architecture and describes the capabilities provided by each component in the Gimmal Discover suite.
Architecture
Gimmal Discover is an on-demand platform that combines a hosted service with software components installed locally at each client site. This architecture offers organizations a secure method for managing their data on-site, thereby eliminating the need to store sensitive information in the cloud. The diagram below outlines a typical configuration of Gimmal Discover:
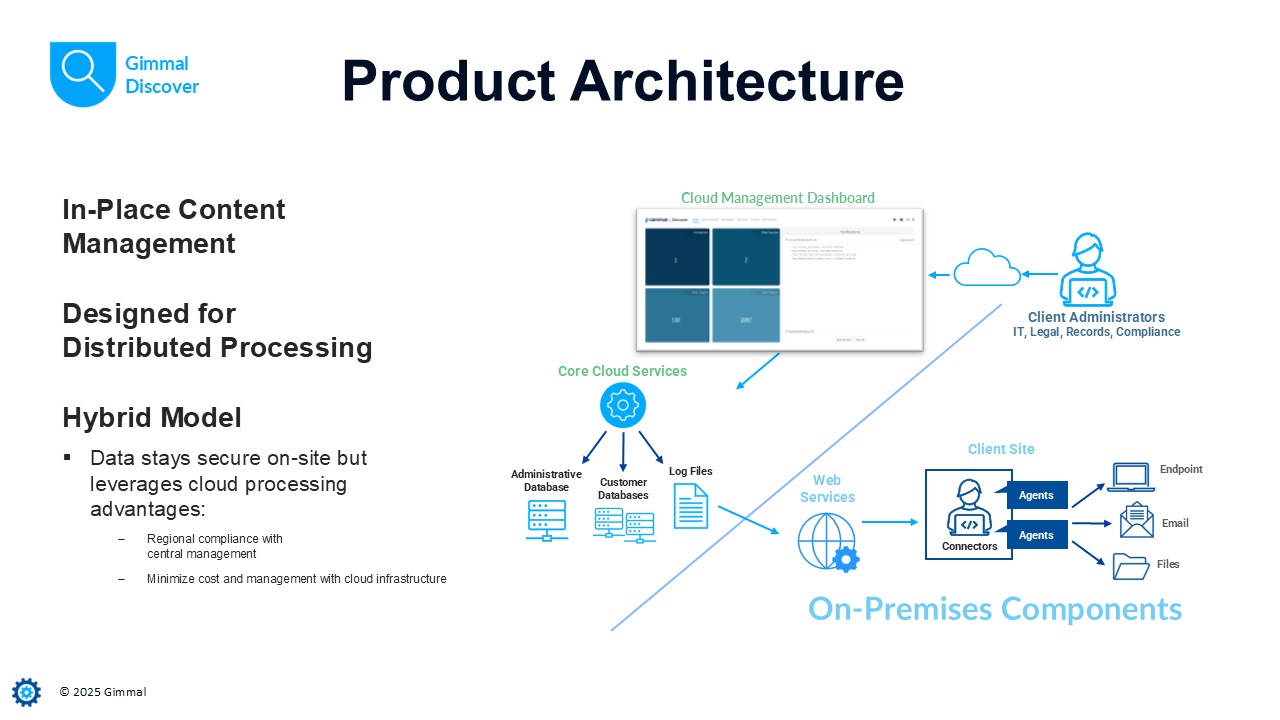
Discover Architecture
The hosted component of Gimmal Discover features a sophisticated management dashboard, composed of SSL-secured web modules. This dashboard enables administrators to effortlessly configure services, establish policies, analyze content, and execute eDiscovery searches. Accessible via a secure login page on any standard web browser, the dashboard ensures user-specific roles dictate individual privileges within the Discover platform.
Components
Connectors
Client sites are interconnected with the management dashboard in the cloud through software components known as Connectors. The Discover Connector component regularly polls the management dashboard to check for new requests and relay information from Agents back to the Discover hosted environment. Connectors are installed as a Microsoft Windows service and leverage Microsoft’s Windows Communication Foundation (WCF) framework. WCF serves as Microsoft’s unified programming model for developing service-oriented applications, enabling developers to create secure, reliable, and transactional solutions that integrate across various platforms and interoperate with existing environments.
Discover Connectors utilize HTTPS for communication with the hosted web services, ensuring data encryption during transit. This protocol is advantageous as most organizations already permit port 443 traffic through their firewall. The Connector setup application can be downloaded from the Discover dashboard by clicking on Administration and then selecting the Download Center link in the left navigation pane. Connectors are typically installed on any network endpoint that requires content management (files, email, etc.). In many cases, managing an email server for example, a single Connector installed on an application server (physical or virtual) is all that is required. Organizations that wish to manage individual user machines (i.e., documents on a local hard drive) install a Connector on each device that requires management, this is usually done using a software patch management tool such as Microsoft SCCM to distribute and execute a silent installer package. Once installed, each registered Connector will display in the management console under the Administration/Configuration area..
Discover Connector
Agents
Discover Agents are client-side software components installed on devices where Connectors are already registered. Agents are designed to process a particular type of unstructured data.
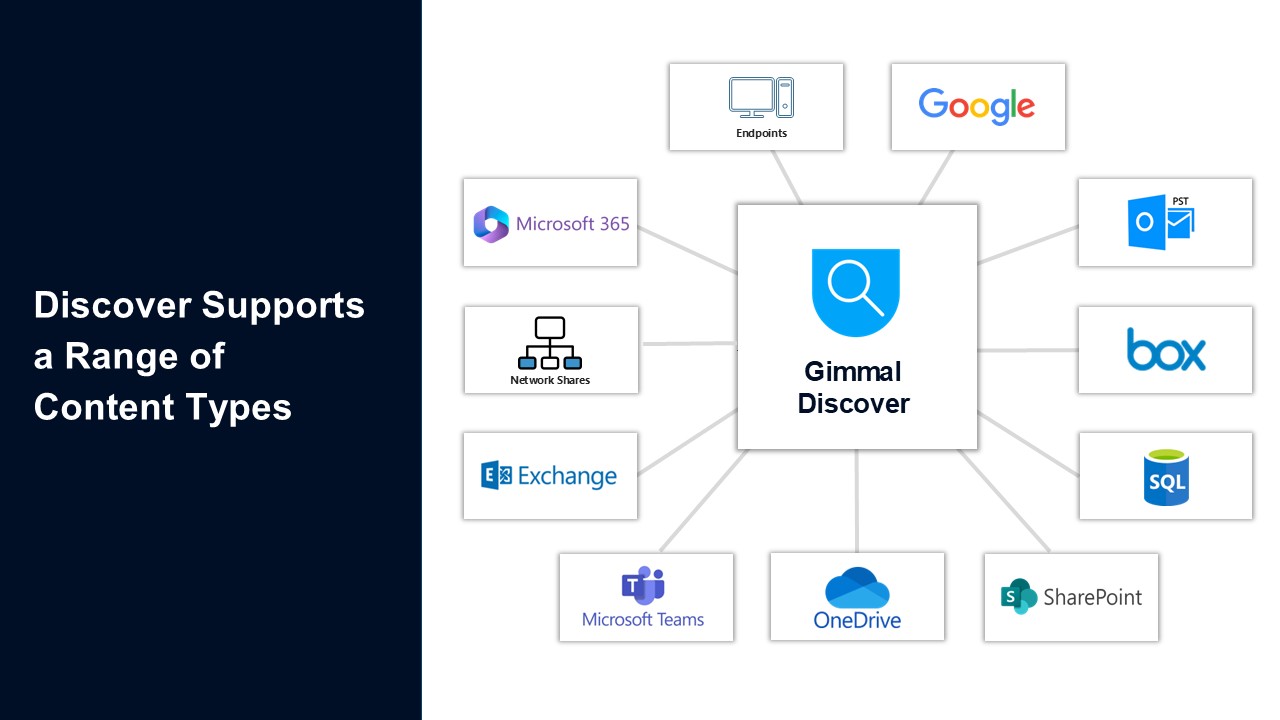
Content Sources Supported
The list of available Discover Agents includes:
MAPI Agent provides policy processing capabilities for Microsoft Exchange mailboxes, archives, and PST files.
EWS Agent provides policy processing capabilities for Microsoft Exchange mailboxes or archives hosted in the Microsoft 365 cloud and for on-premises versions of Exchange 2016.
File Agent provides policy processing for the file-based content resident on any computer managed by a Windows operating system (i.e., local drives or network file shares).
SharePoint Agent provides policy processing for both local and hosted versions of SharePoint.
OneDrive Agent supports access to content in the Microsoft OneDrive for business cloud.
Google Workspace Agent allows access to Gmail and GDrive repositories in Google Workspace.
OLEDB Agent supports access to a variety of SQL based structured data including SQL Server, MySQL, and PostgreSQL.
Box Agent supports content stored in the Box cloud storage platform.
MSGraph Agent supports content stored in Microsoft Teams.
Upon launching the Connector setup utility, administrators are prompted to select the content sources that Discover will manage. Based on these selections, the Connector will automatically download, install, and configure the corresponding Agents. Furthermore, additional Agents can be integrated into an existing Connector through the Discover dashboard. As new versions are released, both the Connector and its Agents will receive automatic updates.
Agents are installed as a Microsoft Windows service, utilizing either a designated domain login account or, for workstations, the built-in Windows Local System account. The credentials for the service account are securely retained on the local machine where the agent is installed. Importantly, the hosted portion of Discover does not store any service account login information, thereby enhancing the protection of the client’s environment.
In the Administration/Configuration section of the Discover dashboard, there is a link labeled 'Data Sources.' Data Sources represent categories of unstructured content identified by Discover, such as mailboxes, PST files, and network shares. Once the Connectors and Agents are installed, administrators can initiate searches for specific content types (e.g., locate all mailboxes) and designate those searches to be executed by a Connector. The results returned from these searches, which may include items like mailboxes, PST files, or file paths, are referred to as 'data targets'. From the dashboard, administrators have the ability to link data targets with their respective owners (or custodians) to facilitate policy management, reporting, or eDiscovery activities.
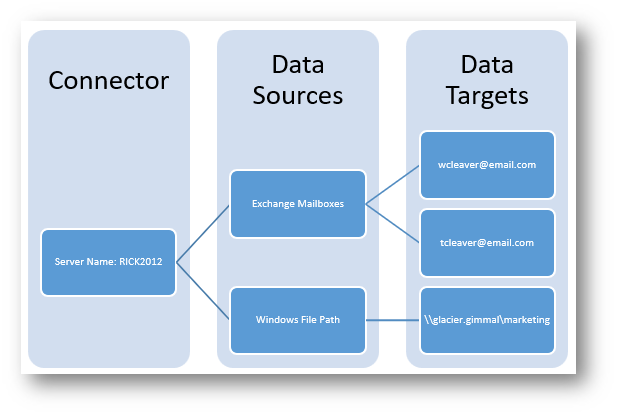
Discover Data Target Hierarchy
Discover Components
Discover is specifically licensed to meet distinct business requirements. This section offers a comprehensive overview of the four key components currently available: Data Governance, Classification, eDiscovery, and Analytics.
Data Governance
Discover policies can be utilized to enforce actions, such as defensibly deleting information, or to generate reports. Each policy consists of the following components:
A workflow that determines the business rules applied to the content.
Targets that can include individuals, devices, or groups (Discover provides various grouping mechanisms).
An optional schedule that allows policies to be executed on-demand or configured for recurring runs based on a specified timetable.
From an operational standpoint, when a policy is initiated, either manually or through a schedule, it generates a queued request for each Connector. The Connector periodically checks in with Discover to see if there are any pending database requests for its managed Agents. It's crucial to understand that the Connector is responsible for initiating all communications with the cloud, minimizing the need for custom firewall configurations, and mitigating concerns about potential tampering during communication sessions.
When a Connector check-in occurs and finds a policy is waiting for one of its Agents, the policy manifest is downloaded for local execution. The Agent then connects to the specified managed target (e.g., a mailbox), applies the business logic defined in the policy workflow, and sends relevant results (such as reports and log files) back to the Connector. The Connector subsequently relays that information back to the hosted environment. Once all Agents assigned to a policy have either reported back or exceeded their timeout period, the policy is marked as complete, and the log files are transferred from the Connectors to the Discover dashboard, thereby creating a comprehensive audit trail.
Workflows
Workflows
Discover policies utilize workflows to map out the sequence of steps that will take place when a policy is executed. Workflows are developed using either the simplified web editor or a desktop application called the Workflow Editor which is available from the Discover download center. This editor provides a flowchart-like interface for designing complex workflows. The diagram below shows the web view of a workflow that is designed to create an inventory report of files exceeding 5 MB in size.
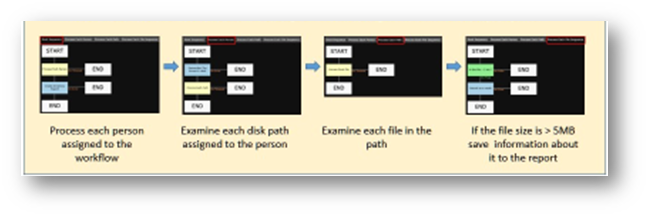
Workflow Architecture
The Workflow Editor communicates with the Discover dashboard, allowing authorized users to save workflows to the hosted site or download workflows created in the web editor for additional edits. Once a workflow has been saved to the dashboard, it becomes available to be used for a policy.
Policies
A policy provides the implementation package for each Discover workflow. When creating a policy, clients provide instructions on how the workflow should be executed (for example run in live or test mode), what data targets the workflow should process (i.e. workstations, mailboxes, file shares, etc.) and whether the policy should be triggered automatically on a scheduled basis.
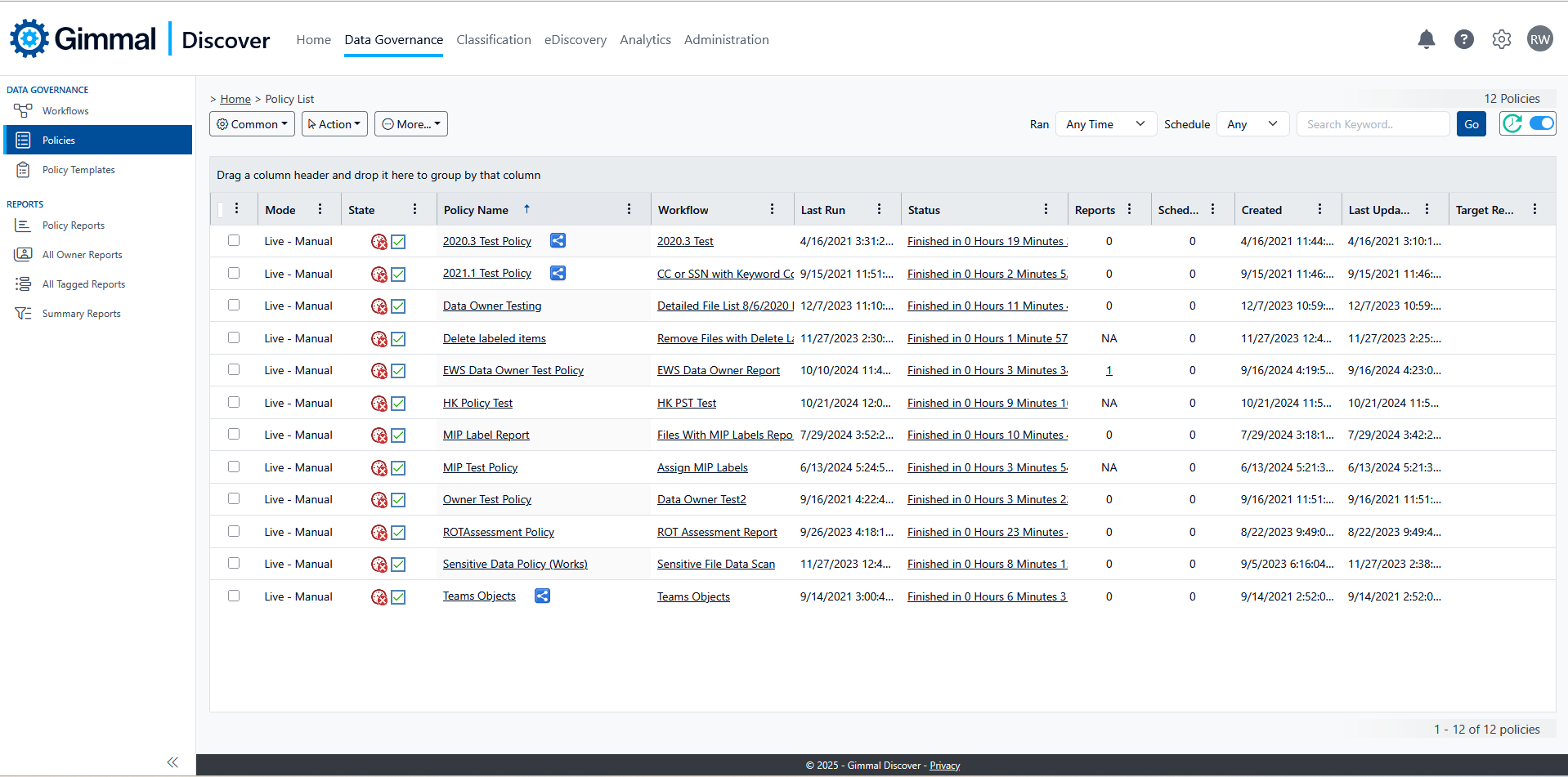
Data Governance Policies
Classification
Discover Classification provides a way to categorize any data target by applying a label (or tag) to the meta-data of the item. Once these labels have been applied, they travel with the file, email, etc., and may be used as criteria for selecting an item to process in Data Governance (i.e. apply a 5-year retention period to any confidential item) or to select specific categories of content to be included in an eDiscovery search (for example skip every file classified as private).
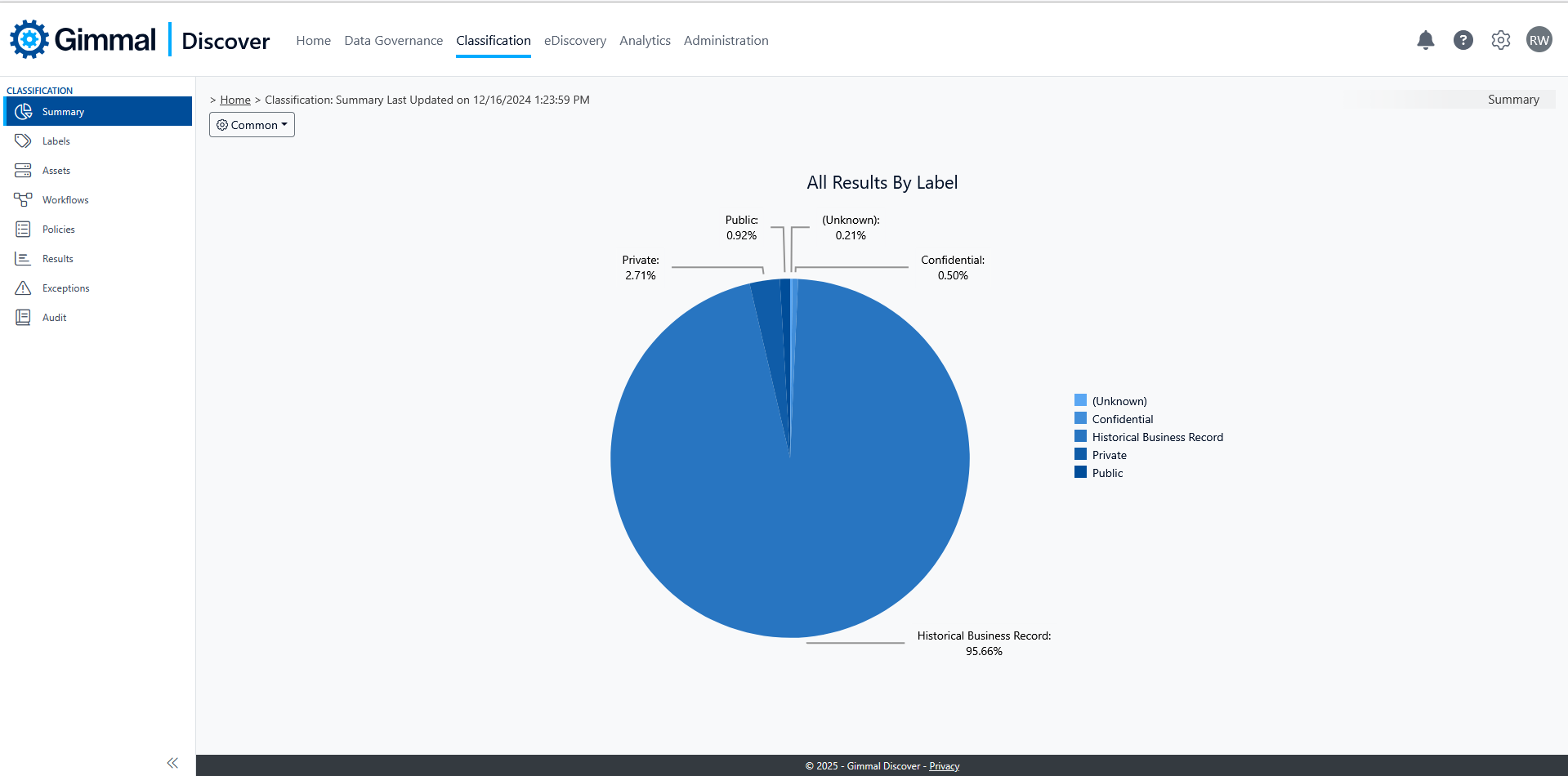
Classification
eDiscovery
eDiscovery allows IT and legal teams to efficiently collaborate while performing searches for litigation, freedom of information requests, or privacy. These search results may then be reviewed for relevancy and the responsive results collected. Apart from collection, eDiscovery features are powered by the same Discover Agents used for policies or reporting which simplifies the implementation process. If your team plans to generate a final set of data for import into a legal review tool simply deploy the collection agent – this component is designed to make a forensically sound copy of tagged search results to a secure location within your network. To aid in the review process Discover also features a user role for eDiscovery reviewers – this role is pre-built to provide just the access rights needed to review search results and is an ideal way of collaborating with a third-party partner such as outside counsel.
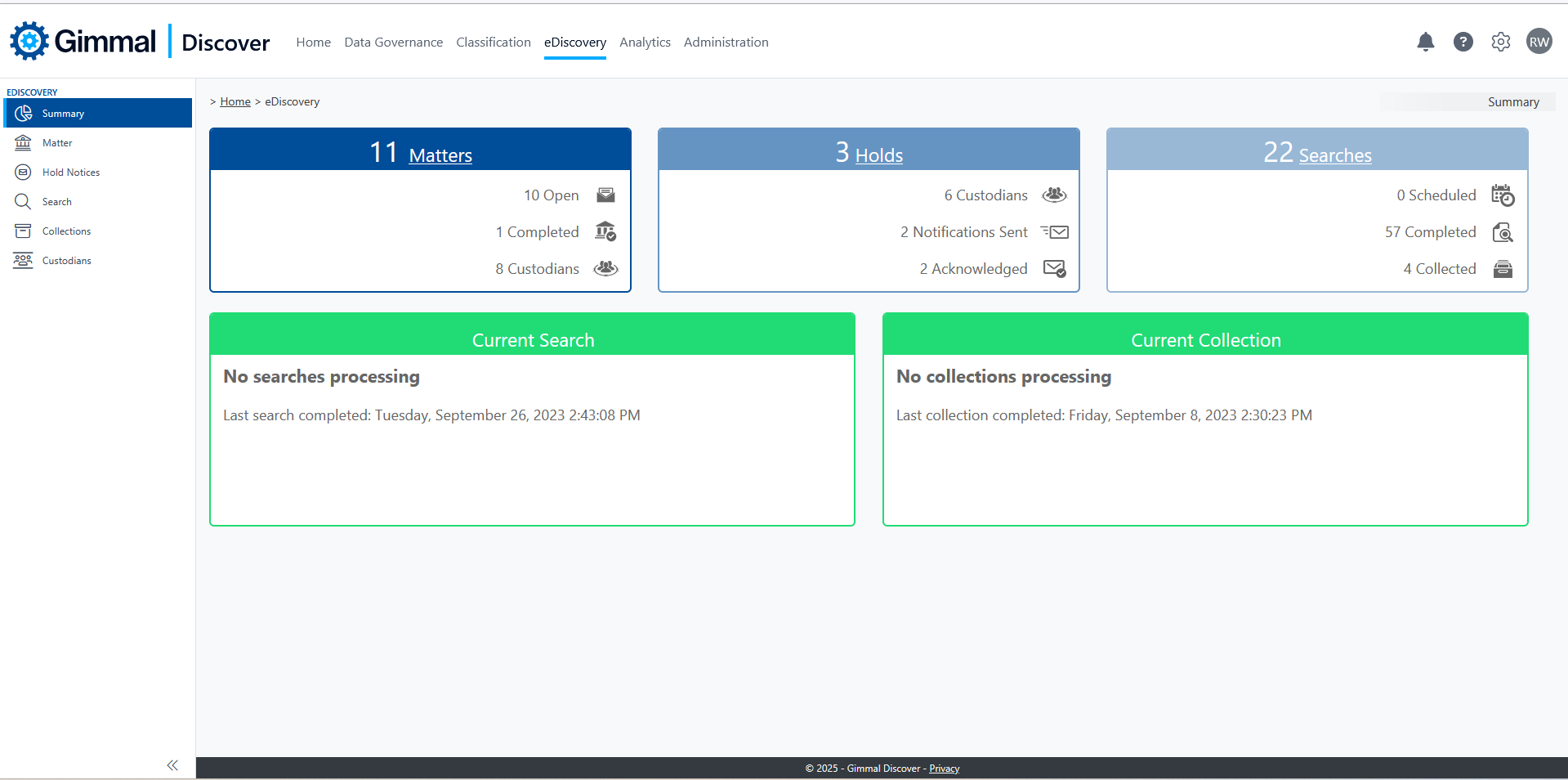
eDiscovery
Analytics
Discover Analytics provides important insights into your content. Analyze unstructured data by age, size, or type to determine how much redundant, outdated, or trivial information may be latent in your content repositories. Discover analytics may be viewed in easy-to-understand charts or presented in a trend analysis form to track performance over time. In addition to the pre-built analytics included, custom ad-hoc reports may be generated through a Discover workflow and viewed or shared from the reporting area in Data Governance.
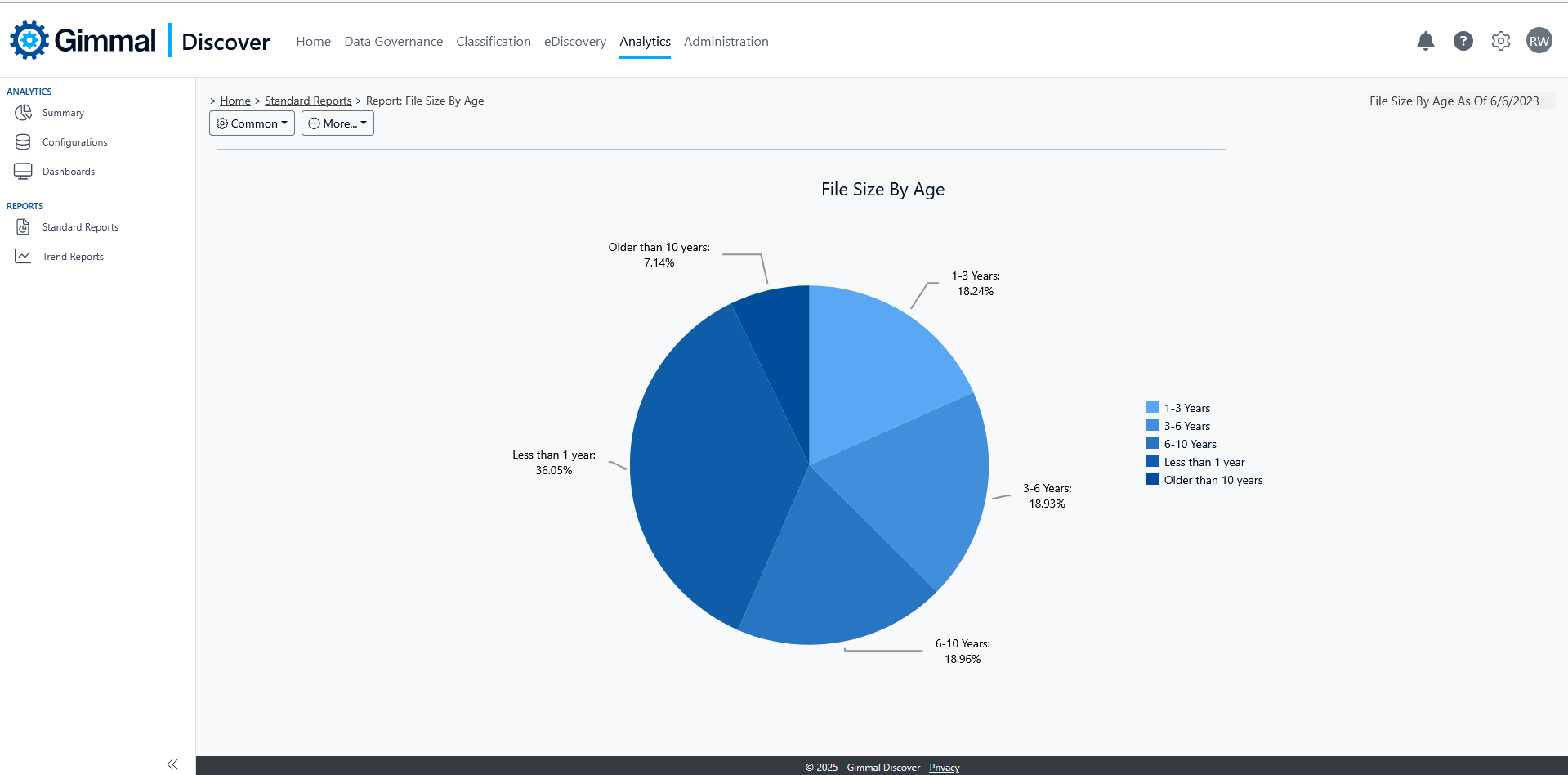
File Age Analytics
Synopsis
Discover provides a highly secure and extremely flexible platform for managing unstructured data. Since Discover is offered on-demand it requires less client infrastructure (servers, databases, etc.) leading to a very rapid implementation cycle. This same architecture makes it ideally suited to organizations that must enforce policies across a widely dispersed workforce. Most importantly, clients have the assurance of knowing that both their policies and eDiscovery searches are being applied within their networks and no business-critical information is being stored in the cloud. For more information, please contact your Gimmal sales representative or visit the Discover page at Gimmal.com.
